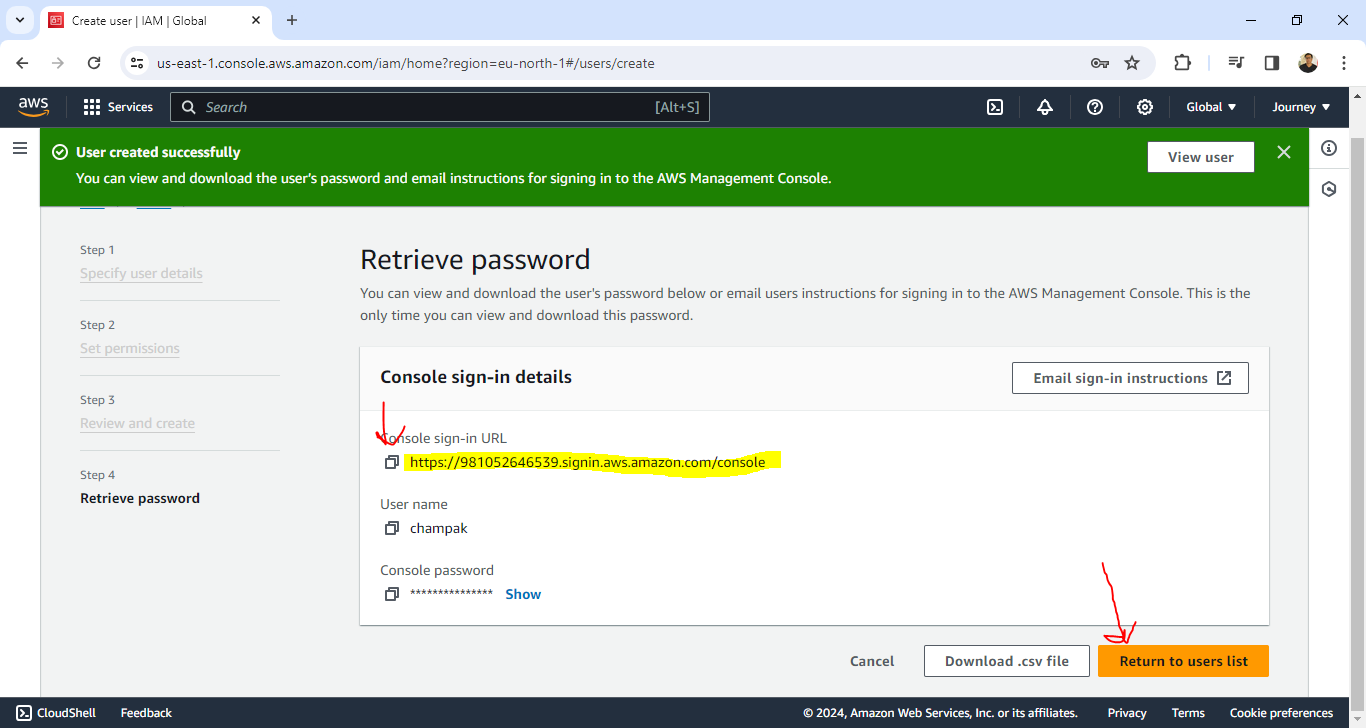
Creating an AWS - IAM User
Navigating AWS Security: The Vital Role of IAM Users
In the sprawling ecosystem of Amazon Web Services (AWS), effective security management is paramount. Among the array of tools and features designed to safeguard your digital assets, Identity and Access Management (IAM) stands out as a cornerstone. IAM users, in particular, play a crucial role in fortifying your AWS infrastructure against unauthorized access and ensuring the principle of least privilege. Let's delve into their significance and explore how they contribute to a robust security posture in the AWS cloud environment.
### Understanding IAM Users
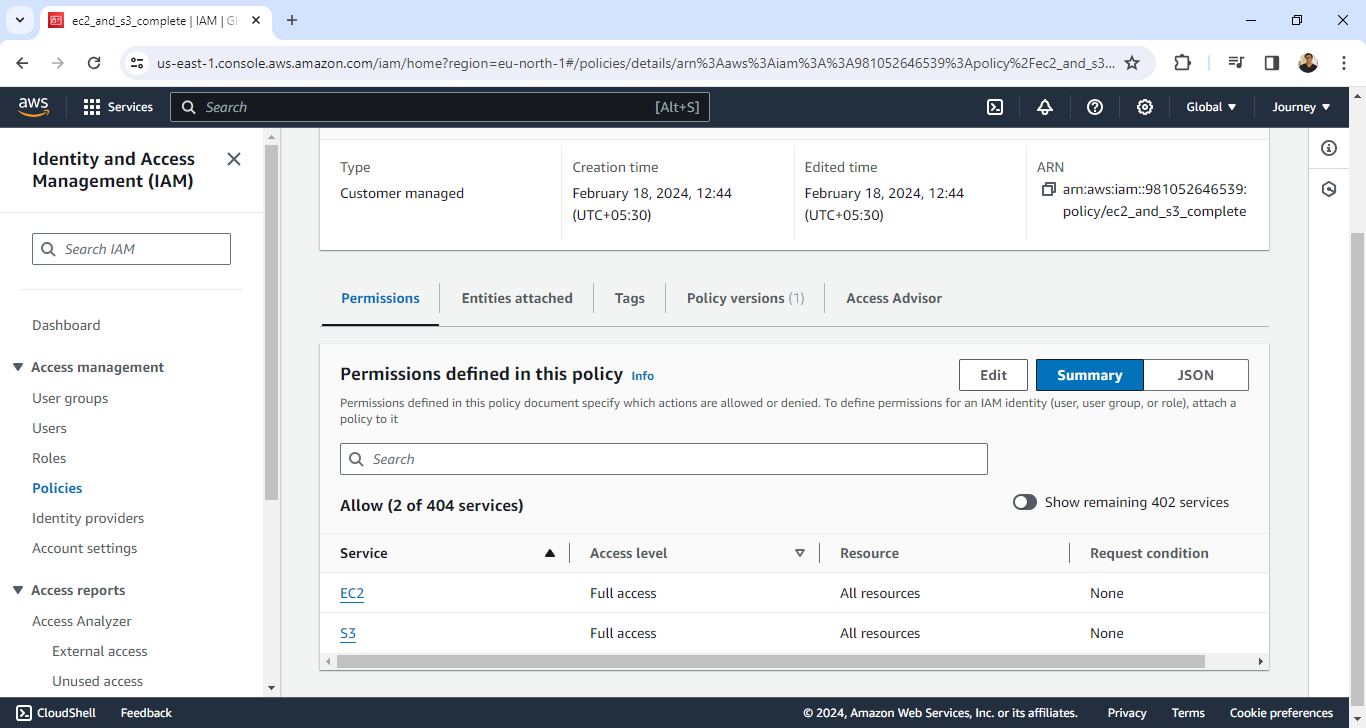
IAM users are entities with unique credentials used to interact with AWS services programmatically or through the AWS Management Console. Unlike the AWS account root user, which possesses unrestricted access to all AWS resources, IAM users offer a more granular approach to access control. Each IAM user is assigned specific permissions delineated by policies, which define the actions they can perform and the resources they can access within your AWS account.
### Importance of IAM Users
#### 1. Principle of Least Privilege (PoLP)
IAM users enable the implementation of the principle of least privilege, a fundamental tenet of security best practices. By granting only the permissions necessary for their respective roles, IAM users minimize the risk of unauthorized access and limit the potential damage of a compromised account. This fine-grained control reduces the attack surface and enhances overall security posture.
#### 2. Segregation of Duties
In complex organizations with diverse teams and responsibilities, IAM users facilitate the segregation of duties. Different users can be assigned distinct roles aligned with their job functions, ensuring that individuals have access only to the resources essential for their tasks. This separation enhances accountability, prevents conflicts of interest, and mitigates the risk of insider threats.
#### 3. Auditing and Compliance
IAM user activity is logged and auditable, providing invaluable insights into resource usage and access patterns. By monitoring IAM user actions, organizations can detect suspicious behavior, unauthorized access attempts, or deviations from established policies. These audit trails are indispensable for regulatory compliance, internal governance, and incident response efforts.
#### 4. Scalability and Flexibility
As AWS environments evolve and expand, the management of user access can become increasingly complex. IAM users offer scalability and flexibility, allowing organizations to adapt their access control mechanisms to changing requirements seamlessly. Whether provisioning new users, modifying permissions, or revoking access, IAM provides the agility necessary to align security measures with evolving business needs.
#### 5. Integration with Identity Providers
IAM users can be federated with external identity providers (IdPs) using standards such as Security Assertion Markup Language (SAML) or OpenID Connect. This integration streamlines user management processes by leveraging existing authentication mechanisms and centralizing access control policies. By integrating IAM with corporate directories or identity federation services, organizations can enhance security while simplifying user provisioning and authentication workflows.
### Best Practices for Managing IAM Users
To maximize the effectiveness of IAM users in AWS security, adhere to these best practices:
1. **Implement Role-Based Access Control (RBAC):** Define roles based on job functions and assign permissions accordingly to enforce the principle of least privilege.
2. **Regularly Review and Revise Permissions:** Conduct periodic audits to ensure that IAM policies align with business requirements and security standards, modifying permissions as necessary.
3. **Enable Multi-Factor Authentication (MFA):** Require IAM users to authenticate using multiple factors, such as passwords and one-time codes, to add an extra layer of security.
4. **Utilize IAM Access Analyzer:** Leverage AWS IAM Access Analyzer to continuously monitor resource policies and detect unintended access, helping to maintain a secure configuration.
5. **Implement IAM Password Policies:** Enforce strong password policies for IAM users, including requirements for complexity, rotation, and expiration, to mitigate the risk of credential-based attacks.
6. **Monitor IAM User Activity:** Utilize AWS CloudTrail to log IAM user actions and analyze activity logs for security monitoring, compliance, and troubleshooting purposes.
In conclusion, IAM users are indispensable components of AWS security architecture, enabling organizations to enforce access control, adhere to compliance requirements, and bolster overall resilience against cyber threats. By embracing IAM best practices and integrating user management into their security strategy, AWS customers can confidently navigate the cloud landscape while safeguarding their digital assets from unauthorized access and malicious activities.



























.png)